User Experience Flow
The following details the Interac Hub user experience flow at a high level. All user interface elements are provided and hosted directly on the Interac Hub, and there is no expectation for the relying party to build any UI elements.
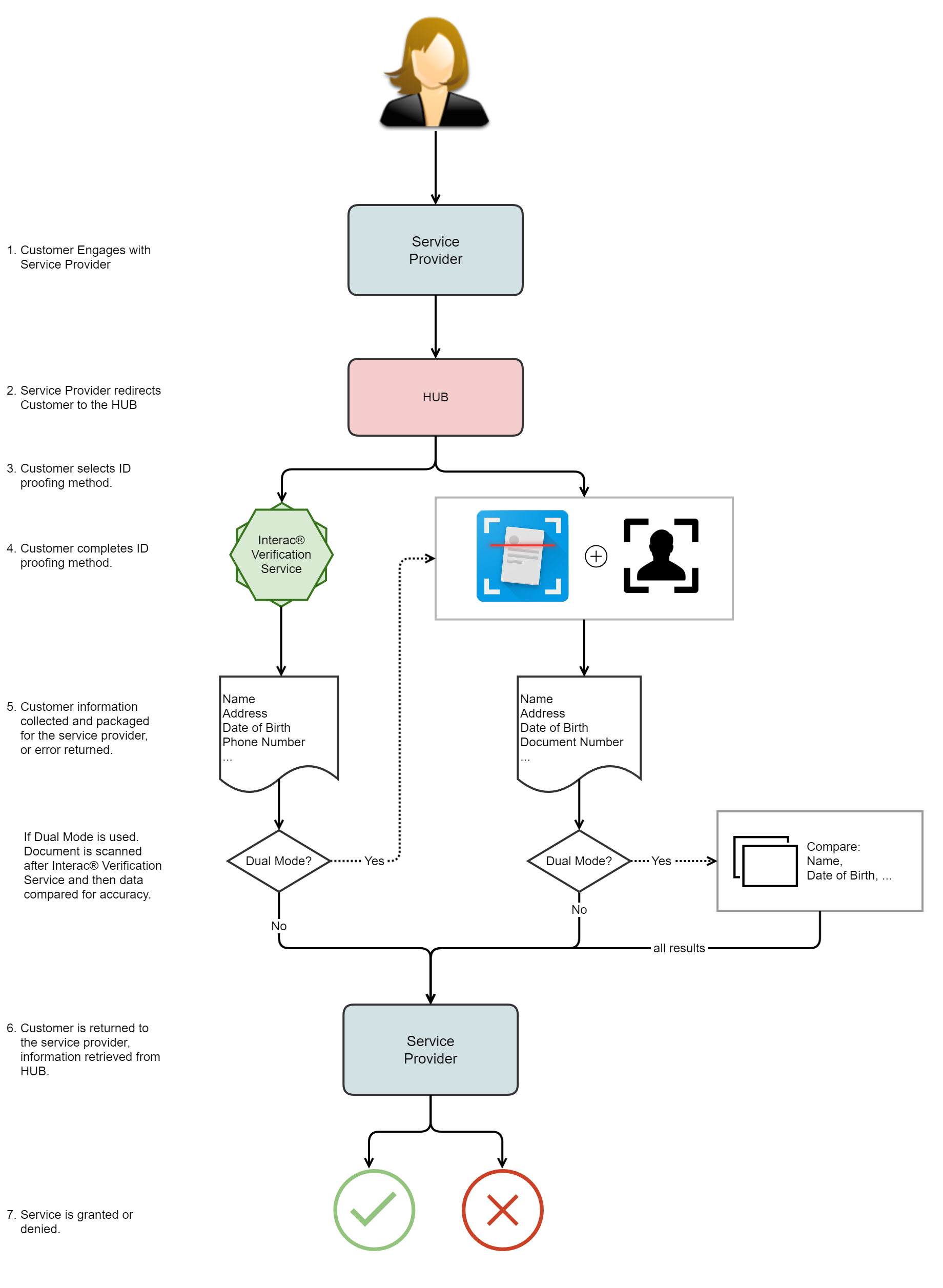
- Customer Engages with Service Provider: On the service provider (i.e. relying party) website / mobile app, the user clicks a link to initiate ID verification as part of some user journey (e.g. applying for a product/service where ID verification is required).
- Service provider redirects Customer to the HUB: The link the user clicks on sends a request to the Hub API, and the response is a subsequent link/redirect bringing the user to the Interac Hub landing page. A series of steps will be presented to the user to guide him/her through the ID verification process.
- Customer selects ID proofing method: The Interac Hub user interface will allow the user to complete ID verification by either selecting financial institution authentication or government ID verification. Relying parties will be able to control whether one or the other, or both are selectable.
- Customer completes ID proofing method: The user will be redirected to the relevant Interac Hub user interface to perform their chosen form of ID verification.
- Customer information collected...: After the user provides consent on the Interac Hub user interface, the ID verification details will be provided back to the relying party in the form of an HTTP API response (JSON data format).
- Customer is returned to the service provider: The Interac Hub user interface redirects the user back to the relying party's website / mobile app where the user originally started the ID verification flow. This allows the user journey to continue at the relying party solution based on the ID verification results.
It is expected that the relying party take all measures to ensure that the ID verification details received from the Interac Hub matches with the current user session. This ensures that the user claims received are applied to the correct user session/end user on the relying party's side.
Updated over 2 years ago